病毒样本:ntldr.exe
大小:28,000 字节
MD5: B08791CB82AB0E9065CE2CBE3864300D
Upack V0.36-V0.37 (DLL) -> Dwing
传播方式:U盘传播
病毒类型:下载者
1,运行C:\ntldr.exe后,自删除,复制到自己到各个分区跟目录。
释放文件
C:\WINDOWS\Fonts\00-03-FF-02-32-34\system\wdfmgr.exe
C:\WINDOWS\system32\DRIVERS\msaclue.sys
c:\windows\upxdnd.exe
启动wdfmgr.exe。
添加自启动run值:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
TBMonEx c:\windows\fonts\00-03-ff-02-32-34\system\wdfmgr.exe
upxdnd c:\windows\upxdnd.exe
添加服务:
HKLM\SYSTEM\CurrentControlSet\Services\msskye
ImagePath:C:\WINDOWS\system32\DRIVERS\msaclue.sys
2,访问m.8q8.biz/xin.jpg获取更新信息。之后开始疯狂下载。
http://a.935425.com( 58.53.128.92)/00006.exe
http://a.935425.com( 58.53.128.92)/00007.exe
http://a.935425.com( 58.53.128.92)/00009.exe
http://a.935425.com( 58.53.128.92)/00011.exe
http://qq.935425.com( 59.60.150.86)/00008.exe
http://qq.935425.com( 59.60.150.86)/00025.exe
http://qq.935425.com( 59.60.150.86)/arp111.exe
http://f.935425.com(59.60.157.34)/00013.exe
http://f.935425.com(59.60.157.34)/00012.exe
http://f.935425.com(59.60.157.34)/00015.exe
http://f.935425.com(59.60.157.34)/00016.exe
http://f.935425.com(59.60.157.34)/00017.exe
http://f.935425.com(59.60.157.34)/00033.exe
http://g.935425.com(59.60.146.78)/00018.exe
http://g.935425.com(59.60.146.78)/00019.exe
http://g.935425.com(59.60.146.78)/00024.exe
http://g.935425.com(59.60.146.78)/00021.exe
http://g.935425.com(59.60.146.78)/jz.exe
3,这些文件运行后。
释放文件:
c:\motou.exe
c:\smss.com
c:\smss.exe
C:\WINDOWS\system32\ntvdm.exe
C:\WINDOWS\system32\drivers\msaclue.sys
C:\WINDOWS\system32\wpcap.dll
C:\WINDOWS\system32\wanpacket.dll
C:\WINDOWS\system32\upxdnd.dll
C:\WINDOWS\system32\rpcapd.exe
C:\WINDOWS\system32\qlihzouhgnfe.dll
C:\WINDOWS\system32\pthreadVC.dll
C:\WINDOWS\system32\packet.dll
C:\WINDOWS\system32\npf_mgm.exe
C:\WINDOWS\system32\NetMonInstaller.exe
C:\WINDOWS\system32\nahzij.dll
C:\WINDOWS\system32\LotusHlp.dll
C:\WINDOWS\system32\ijiq.dll
C:\WINDOWS\system32\daemon_mgm.exe
C:\WINDOWS\Fonts\00-03-FF-02-32-34\system\wdfmgr.exe(先前释放)
C:\WINDOWS\Fonts\00-03-FF-02-32-34\system\KB930.vxd
C:\WINDOWS\Fonts\00-03-FF-02-32-34\system\00011.exe
C:\WINDOWS\Fonts\00-03-FF-02-32-34\system\00009.exe
C:\WINDOWS\Fonts\00-03-FF-02-32-34\system\00006.exe
C:\WINDOWS\Fonts\00-03-FF-02-32-34\system\00007.exe
C:\WINDOWS\Fonts\jsqxczc.exe
C:\WINDOWS\Fonts\jsqxcyc.dll
C:\WINDOWS\Fonts\jsqxcss.dll
C:\WINDOWS\Fonts\jshubxw.fon
C:\WINDOWS\LotusHlp.exe
C:\WINDOWS\upxdnd.exe(先前释放)
x:\ntldr.exe
x:\autorun.inf
X代表各分区盘符
添加run值:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
LotusHlp c:\windows\lotushlp.exe
InternetExe C:\motou.exe
添加ShellExecuteHooks:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks
注册表值: {3D098345-9012-8750-8910-9128098134D3}
HKCR\CLSID\{3D098345-9012-8750-8910-9128098134D3}\InprocServer32
注册表值: C:\WINDOWS\Fonts\jsqxcyc.dll
4,安装WinPcap,用于局域网arp欺骗。
命令:
smss.exe” -idx 0 -ip 192.168.1.2-192.168.1.253 -port 80 -insert ”
”
5,映象劫持下列软件
360rpt.exe
360Safe.exe
360tray.exe
ACKWIN32.EXE
ANTI-TROJAN.EXE
apitrap.dll
APVXDWIN.EXE
ASSTE.dll
AUTODOWN.EXE
AVCONSOL.EXE
AVE32.EXE
AVGCTRL.EXE
AVKSERV.EXE
AVNT.EXE
AVP.EXE
AVP32.EXE
AVPCC.EXE
AVPDOS32.EXE
AVPM.EXE
AVPTC32.EXE
AVPUPD.EXE
AVSCHED32.EXE
AVSTE.dll
AVWIN95.EXE
AVWUPD32.EXE
BLACKD.EXE
BLACKICE.EXE
CFIADMIN.EXE
CFIAUDIT.EXE
CFINET.EXE
CFINET32.EXE
CLAW95.EXE
CLAW95CF.EXE
CLEANER.EXE
CLEANER3.EXE
Cleanup.dll
cqw32.exe
divx.dll
divxdec.ax
DJSMAR00.dll
DRMINST.dll
DVP95.EXE
DVP95_0.EXE
ECENGINE.EXE
EGHOST.EXE
enc98.EXE
EncodeDivXExt.dll
EncryptPatchVer.dll
ESAFE.EXE
EXPWATCH.EXE
F-AGNT95.EXE
F-PROT.EXE
F-PROT95.EXE
F-STOPW.EXE
FESCUE.EXE
FINDVIRU.EXE
FP-WIN.EXE
FPROT.EXE
front.exe
FRW.EXE
fullsoft.dll
GBROWSER.DLL
htmlmarq.ocx
htmlmm.ocx
IAMAPP.EXE
IAMSERV.EXE
IBMASN.EXE
IBMAVSP.EXE
ICLOAD95.EXE
ICLOADNT.EXE
ICMON.EXE
ICSUPP95.EXE
ICSUPPNT.EXE
IFACE.EXE
install.exe
IOMON98.EXE
Iparmor.exe
ishscan.dll
ISSTE.dll
javai.dll
JEDI.EXE
jvm.dll
jvm_g.dll
KAV32.exe
KAVPFW.EXE
KAVsvc.exe
KAVSvcUI.exe
KVFW.EXE
KVMonXP.exe
KVMonXP.kxp
KVSrvXP.exe
KVwsc.exe
KvXP.kxp
KWatchUI.EXE
LOCKDOWN2000.EXE
Logo1_.exe
Logo_1.exe
LOOKOUT.EXE
LUALL.EXE
MAILMON.EXE
main123w.dll
mngreg32.exe
MOOLIVE.EXE
MPFTRAY.EXE
msci_uno.dll
mscoree.dll
mscorsvr.dll
mscorwks.dll
msjava.dll
mso.dll
N32SCANW.EXE
Navapsvc.exe
Navapw32.exe
NAVLU32.EXE
NAVNT.EXE
NAVOPTRF.dll
navw32.EXE
NAVWNT.EXE
NeVideoFX.dll
NISUM.EXE
NMain.exe
NORMIST.EXE
NPMLIC.dll
NSWSTE.dll
NUPGRADE.EXE
NVC95.EXE
PAVCL.EXE
PAVSCHED.EXE
PAVW.EXE
PCCWIN98.EXE
PCFWALLICON.EXE
PERSFW.EXE
PFW.EXE
photohse.EXE
PMSTE.dll
ppw32hlp.dll
printhse.EXE
prwin8.EXE
ps80.EXE
psdmt.exe
qfinder.EXE
qpw.EXE
Rav.exe
RAV7.EXE
RAV7WIN.EXE
RAVmon.exe
RAVmonD.exe
RAVtimer.exe
Rising.exe
SAFEWEB.EXE
salwrap.dll
SCAN32.EXE
SCAN95.EXE
SCANPM.EXE
SCRSCAN.EXE
SERV95.EXE
setup.exe
setup32.dll
sevinst.exe
SMC.EXE
SPHINX.EXE
SWEEP95.EXE
symlcnet.dll
TBSCAN.EXE
TCA.EXE
tcore_ebook.dll
TDS2-98.EXE
TDS2-NT.EXE
TFDTCTT8.DLL
THGUARD.EXE
TrojanHunter.exe
ua80.EXE
udtapi.dll
ums.dll
vb40032.dll
vbe6.dll
VET95.EXE
VETTRAY.EXE
VSCAN40.EXE
VSECOMR.EXE
VSHWIN32.EXE
VSSTAT.EXE
WEBSCANX.EXE
WFINDV32.EXE
wpwin8.EXE
xlmlEN.dll
xwsetup.EXE
ZONEALARM.EXE
_AVP32.EXE
_AVPCC.EXE
_AVPM.EXE
_INSTPGM.EXE
修复工具.exe
debugger指向c:\windows\fonts\00-03-ff-02-32-34\system\wdfmgr.exe,实现启动
清除办法:
1,断开网络,不让清除时病毒检测到文件缺失而自动更新
2,打开XDelBoxX,复制上面所列文件(像motou.exe,smss.com,smss.exe,ntldr.exe等几个文件位置视具体情况而定哦),点击右键,选择“从粘贴坂导入”。
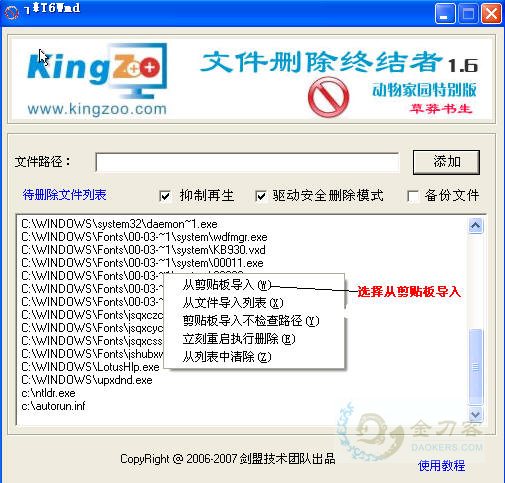
之后选择“立刻重启执行删除”。
3,重启后,打开autoruns.exe,点击“全部启动项”,清除
(1)HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run:
TBMonEx c:\windows\fonts\00-03-ff-02-32-34\system\wdfmgr.exe
upxdnd c:\windows\upxdnd.exe
LotusHlp c:\windows\lotushlp.exe
InternetExe C:\motou.exe
(2)hKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks:
{3D098345-9012-8750-8910-9128098134D3}>
(3)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options:除Your Image…外的所有的内容
(4)HKLM\System\CurrentControlSet\Services(服务)
[Remote Packet Capture Protocol v.0 (experimental) / rpcapd][Stopped/Manual Start]
<"C:\Program Files\WinPcap\rpcapd.exe" -d -f "C:\Program Files\WinPcap\rpcapd.ini">
(5)HKLM\System\CurrentControlSet\Services(驱动)
[msskye / msskye][Running/Auto Start]
[NetGroup Packet Filter Driver / NPF][Running/Manual Start]
如清除run值:
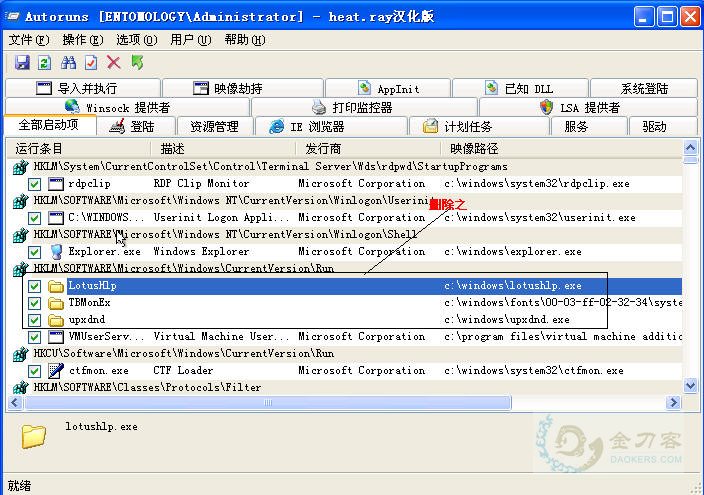
4,下载专杀工具修复被感染文件
5,屏蔽掉这些网站。打开sreng,系统修复,HOST文件,或自己手动用记事本打开C:\WINDOWS\system32\drivers\etc\hosts
添加如下内容:
127.0.0.1 a.935425.com
127.0.0.1 qq.935425.com
127.0.0.1 f.935425.com
127.0.0.1 g.935425.com
127.0.0.1 m.8q8.biz
127.0.0.1 791224.com
保存。
6,升级杀软,全盘扫描。
文件名: ntldr.rar
下载链接:

样本中瑞星杀毒报告:
ijiq.dll>>upack0.34 RootKit.Win32.GameHack.GEN
jsqxcyc.dll Trojan.PSW.Win32.GameOL.GEN
jsqxczc.exe>>upack0.34 Trojan.PSW.Win32.GameOL.lhj
LotusHlp.dll Trojan.PSW.Win32.QQPass.zcz
LotusHlp.exe>>upack0.32 Trojan.PSW.Win32.QQGame.GEN
motou.exe Dropper.Win32.Agent.zfi
nahzij.dll>>upack0.34RootKit.Win32.GameHack.GEN
qlihzouhgnfe.dll>>upack0.34 RootKit.Win32.GameHack.GEN
smss.com>>nspack Dropper.Agent.fxb
smss.exe>>fsg2.0 Trojan.Spy.Agent.dcq
upxdnd.dll Trojan.PSW.Win32.QQGame.GEN
upxdnd.exe>>upack0.32 Trojan.PSW.Win32.GameOL.GEN
wdfmgr.exe>>upack0.34 Worm.Win32.Agent.zil
文件名: logogogo专杀.zip
描述: daokers.com
下载链接:

文件名: logogogo专杀2.zip
描述: daokers.com
下载链接:

附:
点击下载金刀客工具包 (含本文中涉及的所有工具)
病毒上报信箱: daokers@qq.com